IIS has its own security configuration and even for any request reaching the ASP.NET runtime, IIS verifies the request with it's own security configuration. So the first gatekeeper in the ASP.NET security pipeline is actually IIS. So let us understand those security mechanisms which IIS implements:
1. Authentication: IIS support following authentication mechanism
- Basic authentication
- Digest authentication
- Passport authentication
- Window authentication
- Certificate authentication
Point to remember:
- Any authentication which IIS performs results into an authenticated window user, so this means that IIS supports authenticating window users only.
- If ASP.NET is configured to support form or window authentication, then configure IIS to support basic or digest authentication.
- If ASP.NET is configured to support form or custom authentication, then configure IIS to support anonymous access.
- With XP, it comes with IIS 5.x
- With Server 2003, it is IIS 6.0
How to configure IIS for authentication:
Point to member here:
1. When the Anonymous User option is checked then everyone is given access to a web page and it overrides all authentication settings.
2. If IIS is configured to anonymous authentication, we can still use ASP.NET-based security to authenticate users either with ASP.NET-integrated mechanisms such as forms authentication or a custom type of authentication.
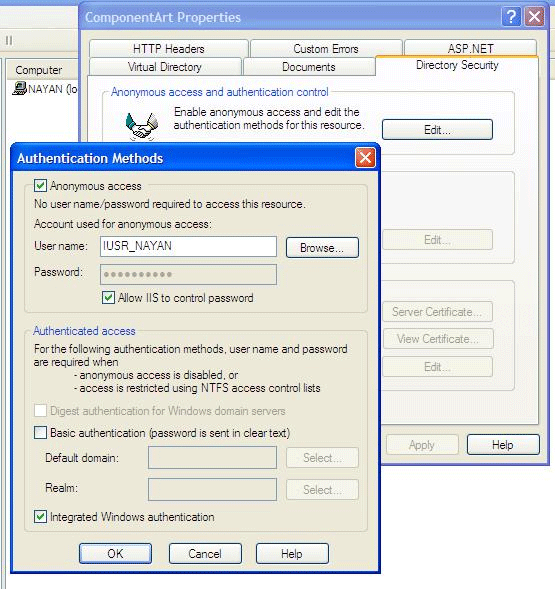
3. Windows authentication configures IIS to validate the credentials of the user against a Windows account configured either on the local machine or within the domain. A Credential submitted by a user is verified against the Windows account.
4. When Basic Authentication is checked it defines an additional HTTP header for transmitting user names and password across the wire but nothing is encrypted here. It is transmitted in the form of a base64 encoding.
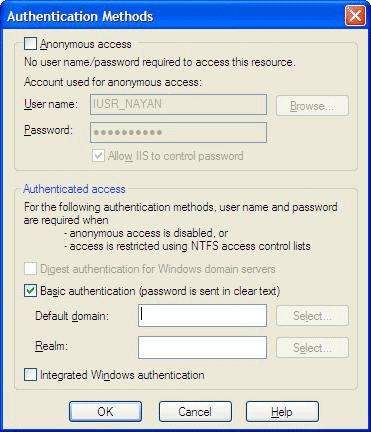
5. Digest authentication is similar to basic authentication with the difference that instead of sending credentials in the form of Base64 encoding, user password and username are hashed.